2 best jobs in the world: A Guide to Google Cyber Security Salary
You know Google Cyber Security Salary reigns supreme, and the demand for skilled Security Engineers and penetration testers has skyrocketed. Among the top contenders in the cybersecurity job market is Google, a tech giant known for its innovative solutions and cutting-edge technology. If you’re considering a career in Google’s cybersecurity realm, one burning question likely echoes in your mind: What is the average Google cyber security salary? Let’s delve into this crucial aspect and unravel the layers of compensation in the fascinating world of Google’s cybersecurity.
Google cyber security salary/roles
To comprehend the intricacies of Google’s cyber security salary structure, it’s imperative to first understand the diverse roles within this domain. From security engineers to penetration testers, each position plays a pivotal role in fortifying Google’s digital fortress. These roles, although varied, share a common thread – safeguarding sensitive information from cyber threats.
Navigating the Maze: Different Roles, Different Payouts
Security Engineers: Google Cyber Security Salary
Security engineers at Google are the architects of digital defense, designing and implementing robust security measures. With responsibilities ranging from system analysis to vulnerability assessments, these professionals play a vital role in ensuring the integrity of Google’s digital infrastructure. The average Google security engineer salary ranges from $120,000 to $160,000 per annum, reflecting the high stakes and responsibilities associated with this role.

Understanding the Role of Security Engineers
Security engineers are the backbone of a robust cybersecurity infrastructure. In essence, they are the guardians of digital realms, responsible for designing, implementing, and maintaining security measures to protect sensitive information. Their roles extend beyond mere code and firewalls; they are strategists in the ever-evolving game of cyber warfare.
The Skill Set of a Security Engineer
To be an effective digital guardian, a security engineer must possess a diverse skill set. Proficiency in programming languages such as Python, Java, and C++ is fundamental. Equally important is an in-depth understanding of networking protocols and systems architecture. Security engineers must be adept at identifying vulnerabilities and crafting solutions to fortify digital fortresses.
Keeping Pace with Evolving Threats
The digital landscape is dynamic, with cyber threats evolving at an alarming rate. Security engineers are not just reactive; they must be proactive in anticipating potential breaches. Continuous learning and staying abreast of emerging technologies are integral parts of their job. From artificial intelligence to blockchain, security engineers must understand the nuances of cutting-edge tools to stay one step ahead of cybercriminals.
The Role of Security Engineers in Business
As businesses increasingly digitize their operations, the role of security engineers becomes even more critical. They are the custodians of customer trust, ensuring that sensitive data remains confidential and systems remain operational. A security breach can have severe repercussions, both financially and reputationally. Therefore, organizations invest heavily in skilled security engineers to protect their digital assets.
Implementing robust Security Protocols
One of the primary responsibilities of security engineers is to design and implement robust security protocols. This includes setting up firewalls, intrusion detection systems, and encryption methods. The mantra is prevention first, mitigation second. By meticulously planning and implementing security measures, they create layers of defense, making it arduous for cyber threats to breach the system.
Collaborating Across Teams
Effective cybersecurity is not a one-person job. Security engineers collaborate across departments, working closely with IT teams, developers, and management to create a comprehensive defense strategy. This collaborative approach ensures that security is integrated into every facet of the organization, from development to deployment.

Emerging Trends in Cybersecurity
The landscape of cybersecurity is ever-changing, and security engineers must stay ahead of the curve. From the rise of cloud security to the integration of machine learning in threat detection, staying updated is crucial. Adaptability is a hallmark of a successful security engineer, ready to tackle new challenges in this dynamic field.
Challenges Faced by Security Engineers
While security engineers play a pivotal role, they are not without challenges. The constantly evolving nature of cyber threats means they are in a perpetual race against time. Additionally, the shortage of skilled cybersecurity professionals adds to the pressure. Organizations must invest in training programs and create an environment that fosters continuous learning to overcome this challenge.
Future Prospects for Security Engineers
As the digital landscape expands, so do the opportunities for security engineers. The demand for skilled professionals in cybersecurity is on the rise, and with advancements in technology, new avenues are opening up. From ethical hacking to threat intelligence analysis, the future looks promising for those choosing a career in digital defense.
Safeguarding the Digital Frontier
Security engineers are the unsung heroes in the digital age, meticulously crafting the defenses that protect our online existence. From preventing data breaches to staying ahead of emerging threats, their role is multifaceted and crucial. As businesses continue to digitize, the demand for skilled security engineers will only intensify, making them the true architects of digital defense. So, the next time you browse securely or make an online transaction without fear, remember, that there’s a security engineer silently working to keep the digital frontier safe.
Penetration Testers: Google Cyber Security Salary
Penetration testers, often referred to as ethical hackers, are tasked with identifying vulnerabilities within Google’s systems before malicious actors can exploit them. This proactive approach to security is crucial in maintaining the integrity of Google’s digital ecosystem. The **average salary for Google penetration testers** hovers around $130,000 to $170,000 annually, making it a lucrative field for cybersecurity enthusiasts.
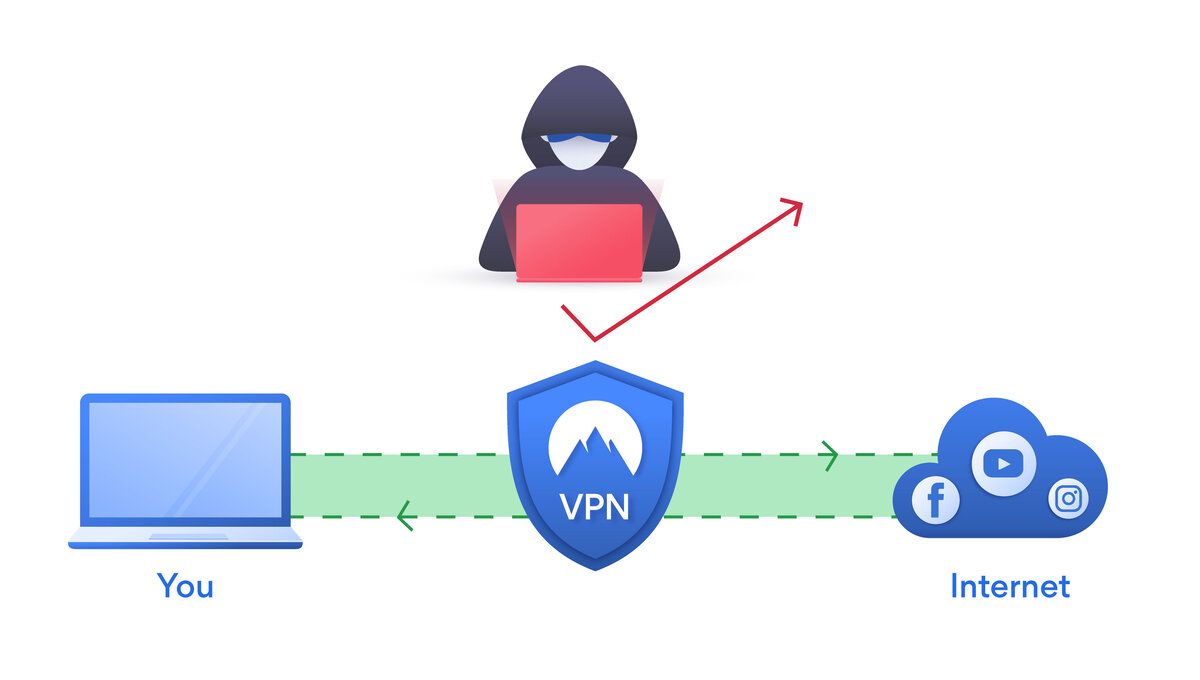
Now businesses are turning to a formidable line of defense known as penetration testers, commonly referred to as ethical hackers. These cybersecurity professionals play a pivotal role in fortifying digital infrastructure against malicious attacks. In this article, we will delve into the world of penetration testers, exploring their responsibilities, methodologies, and the crucial role they play in safeguarding sensitive information.
Understanding Penetration Testing
Penetration testing, often abbreviated as pen testing, is a simulated cyberattack on a computer system, network, or web application to identify vulnerabilities that could be exploited by malicious hackers. Ethical hackers use their skills to mimic the tactics of real cybercriminals, providing organizations with valuable insights into their security posture.
The Role of Penetration Testers
Ethical hackers act as the frontline defense against cyber threats, employing a proactive approach to identify and address vulnerabilities before they can be exploited by malicious actors. Their role goes beyond traditional security measures, focusing on a comprehensive evaluation of an organization’s digital infrastructure.
Methodologies Employed by Ethical Hackers
Reconnaissance: Gathering Intelligence
Before launching an attack, penetration testers engage in thorough reconnaissance to collect information about the target system. This phase involves scanning for publicly available data and identifying potential entry points.
Scanning: Identifying Vulnerabilities
Once the reconnaissance phase is complete, ethical hackers move on to scanning the system for vulnerabilities. This involves using specialized tools to detect weaknesses in the network, applications, or hardware.
Gaining Access: Simulating Cyberattacks
With identified vulnerabilities, penetration testers attempt to exploit them, mimicking the tactics of real hackers. This step is crucial in understanding the extent to which a system can be compromised.
Maintaining Access: Testing Persistence
Ethical hackers assess whether they can maintain access to a system over an extended period. This step simulates scenarios where attackers establish persistence to carry out more prolonged and damaging cyberattacks.
The Importance of Ethical Hacking
In an era where cyber threats are becoming increasingly sophisticated, the importance of ethical hacking cannot be overstated. Here are some key reasons why organizations are investing in penetration testing:
Risk Mitigation: Identifying and Addressing Vulnerabilities
By proactively identifying and addressing vulnerabilities, penetration testers help organizations mitigate the risk of data breaches and cyberattacks. This proactive approach is crucial in preventing potential financial and reputational damage.
Compliance Requirements: Meeting Industry Standards
Many industries have specific cybersecurity compliance requirements. Ethical hacking helps organizations meet these standards, ensuring they adhere to regulations and guidelines set forth by regulatory bodies.
Enhancing Security Awareness: Educating Stakeholders
Ethical hacking not only identifies vulnerabilities but also raises awareness among stakeholders about potential threats. This heightened awareness empowers employees to follow best practices and contribute to overall cybersecurity efforts.
Challenges in Penetration Testing
While penetration testing is a powerful tool in the cybersecurity arsenal, it comes with its set of challenges. These include:
Scope Limitations: Narrowing Down Targets
Defining the scope of a penetration test can be challenging, as organizations need to prioritize specific systems or networks for testing. Ensuring comprehensive coverage within the allotted timeframe is a delicate balance.
False Positives: distinguishing Real Threats
Ethical hackers may encounter false positives, where security tools incorrectly flag certain activities as potential threats. Distinguishing between false positives and actual vulnerabilities requires expertise and careful analysis.
Conclusion
The realm of Google cyber security salaries is as diverse as the roles it encompasses. Whether you’re drawn to the meticulous world of security engineering, the thrill of ethical hacking, or the vigilant eyes of a security analyst, Google offers a spectrum of opportunities with competitive compensation. As you embark on this cybersecurity journey, remember that the pursuit of knowledge, coupled with practical experience and certifications, can unlock doors to a fulfilling and well-compensated career in Google’s cyber defense arena.



